Nerdgasm Examination of a Virus !
I just wanted to start by saying hello my name is Fuzzy and
I am a nerd, with that said I have done two galleries called Nerd-O-Rama showcasing awesome pics of old computers and
horrible wiring re-terminations. I would like to share a blog about something
most people hate but I just cant seem to get enough, the dreaded Virus
programs. Today I will be featuring the last known email blaster program called
Win32\MYDOOM and its variants. The program was Released Between 2004.02.01 and
2004.02.12 the worm perform a DoS attack on the website called www.sco.com. Which was a popular Unix software
solution company, It created 64 threads, which makes an HTTP GET request from a
random port on the infected computer to port 80 of www.sco.com,
similar to now a days programs like low orbit ion cannon (LOIC) that can produce
over 1000 threads and flood server ports making them more vulnerable by giving
the user the ability to manipulated TCP data access, just look at the Sony PS3
accident of April of last year .The
Win32\Mydoom.B variant also attacked
Microsoft in the same manner in the following month, Microsoft even went to the
extent of offering a Bounty of 250,000 USD for the capture of the creator of
the Virus.
Now that you know a brief history of the program lets dissect this beautiful specimen
Infection and delivery
Mydoom can be transmitted through email or file sharing with Kazaa. To be transmitted through Kazaa, the user must download the worm from an infected computer on the Kazaa network.
Mydoom.B also arrived in an email address with a spoofed sender address with eight possible subject lines:
test
hi
hello
Mail Delivery System
Mail Transaction Failed
Server Report
Status
Error
The body of the email could be one of three possibilities:
Mail transaction failed. Partial message is available.
The message contains Unicode characters and has been sent as a binary attachment.
The message cannot be represented in 7-bit ASCII encoding and has been sent as a binary attachment.
The attachment has a generic name and two file extensions in an attempt to fool the user into thinking it is some sort of document. The file name has nine possibilities:
document
readme
doc
text
file
data
test
message
body
now lets dive into its variants
Variant of the Win32\Mydoom
The first fake file extension has three:
htm
txt
doc
The second real file extension has six:
bat
cmd
exe
pif
scr
zip
The .zip version will be an actual .zip file with a copy of the worm bearing the same name as the .zip. If it has an .exe or .scr extension, the attachment will have an icon similar to that of a .txt file in Windows XP.
Here is a picture of the old common icons

What makes it tic ? lets learn about more of the inner workings of the specimen
Initial programming
When Mydoom is executed, it copies itself to the Windows system folder as Taskmon.exe (which is a legitimate file, though only when found in the Windows folder). It also creates the file Shimgapi.dll in the system folder.
Here is what the coding looks like in command string
*do to liability reason I will be only showing a snippet of the coding itself, please do not try to replicate coding or try this at home, I am not reasonable for damages to your hardware, this is merely a learning tool and should only be used as such.
*Re-Named shimgapi.dll as Message.txt
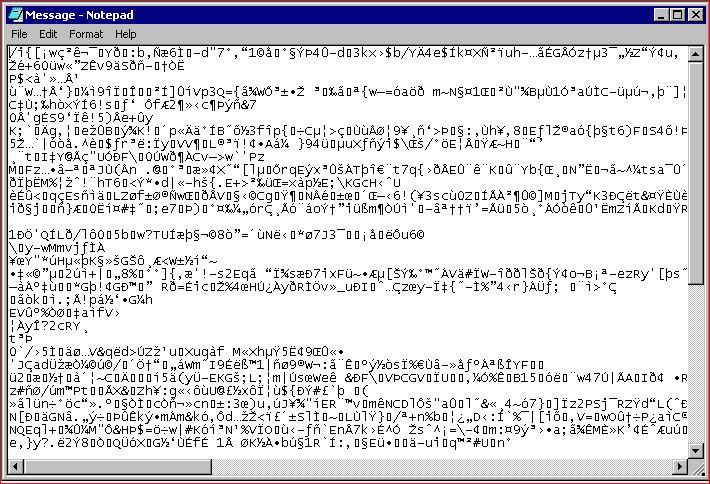
This file is a backdoor trojan that opens TCP listening ports ranging from 3127 to 3198 and can download and execute arbitrary files. A file named Message, which contains random letters when opened with Notepad is placed in the Temp folder and opened in Notepad.
The worm creates or modifies several registry keys. It adds the value "TaskMon = \System Folder\taskmon.exe to two keys, one a Local Machine and the other a Current User registry key, both ensure that the worm will run every time the computer is started. It cradds the value "(Default) = \(System Folder)\shimgapi.dll" to a root registry key that ensures shimgapi.dll will be run by Internet Explorer when the web browser is run. It also creates a Local Machine and current user version of another registry key.
And finally we go conclude with the cause of death!
Cause of Death
The SCO Group, which owns the rights to Unix, sued several
vendors and supporters of Linux, claiming that some of its proprietary code was
used in the system. The company sued Novell (owners of SuSE), AutoZone and
Daimler-Chrysler and was sued by Red Hat and IBM. This action caused much anger
in the open source community, causing many to suspect they were involved. Many
open source groups around the world denied this and condemned the creation of
viruses and worms. Mydoom's origin was traced to Russia when Kaspersky Labs
location-sensing software followed the original emails to ISPs from Russia.
Kaspersky the name you can trust in leading anti-virus programs reversed
engineered the virus and were also successfully able to located and guaranteed
the virus.
Like GIJoe Said Always use Protection when surfing on-line

Hope you enjoyed my blog if this goes well I might do more blogs breaking down other famous Viruses of history .




3 Comments